VMware Horizon Cloud Service Next-Gen – The Automation Series – Chapter 9 – Unified Access Gateway
This blog post is part of the VMware Horizon Cloud Service Next-Gen – The Automation Series, a series of blog posts that describes the possibilities and use of the VMware Horizon Cloud Service Next-Gen APIs.
In this chapter we will add, get and delete Unified Access Gateway deployments. We will use PowerShell to execute the requests. Since Azure is the only provider type supported at the time of writing this chapter, that’s the one we currently focusing on.
The original VMware documentation for Unified Access Gateway operations can be found here.
Create
We will start by creating a Unified Access Gateway deployment. For this we will use the following information:
| HTTP Method | POST | |
| URI | https://cloud.vmwarehorizon.com/admin/v2/uag-deployments | |
| Content-Type | application/json | Header |
| Authorization | Bearer <Access token> | Header |
| name | Name for the UAG deployment | Body |
| description | Description for the UAG deployment | Body |
| orgId | Organization ID | Body |
| fqdn | The fully qualified domain name for the UAG deployment | Body |
| type | The type of UAG deployment, either internal or external | Body |
| providerInstanceId |
The provider instance used for deploying the UAGs | Body |
| numberOfGateways |
The number of UAGs to deploy | Body |
| cluster | The minumum and maximum number of UAGs to deploy | Body |
| sslCertificate | The SSL certificate used for the UAG deployment | Body |
| infrastructure | The required networks/subnets required for the UAG deployment | Body |
With this information we will now construct the lines of code in PowerShell to add the Unified Access Gateway configuration.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 |
$Header = @{ "Content-Type" = "application/json"; "Authorization" = "Bearer " + $AccessToken } $Body = @{ "cluster" = @{ "max" = 2; "min" = 2 } "description" = "My UAGs"; "fqdn" = "uag.domain.com"; "infrastructure" = @{ "dmzNetwork" = @{ "kind" = "subnets"; "id" = "/subscriptions/1x11x11x-11x1-111x-1x11-11111111x11x/resourceGroups/rg-network-horizoncloud/providers/Microsoft.Network/virtualNetworks/vnet-westeurope-horizoncloud/subnets/snet-dmz"; "data" = @{ "parent" = "/subscriptions/1x11x11x-11x1-111x-1x11-11111111x11x/resourceGroups/rg-network-horizoncloud/providers/Microsoft.Network/virtualNetworks/vnet-westeurope-horizoncloud"; "name" = "snet-dmz"; "availableIpAddresses" = 251; "cidr" = "10.21.2.0/24" } }; "managementNetwork" = @{ "kind" = "subnets"; "id" = "/subscriptions/1x11x11x-11x1-111x-1x11-11111111x11x/resourceGroups/rg-network-horizoncloud/providers/Microsoft.Network/virtualNetworks/vnet-westeurope-horizoncloud/subnets/snet-mgmt"; "data" = @{ "parent" = "/subscriptions/1x11x11x-11x1-111x-1x11-11111111x11x/resourceGroups/rg-network-horizoncloud/providers/Microsoft.Network/virtualNetworks/vnet-westeurope-horizoncloud"; "name" = "snet-mgmt"; "availableIpAddresses" = 251; "cidr" = "10.21.0.0/24" } }; "desktopNetwork" = @{ "kind" = "subnets"; "id" = "/subscriptions/1x11x11x-11x1-111x-1x11-11111111x11x/resourceGroups/rg-network-horizoncloud/providers/Microsoft.Network/virtualNetworks/vnet-westeurope-horizoncloud/subnets/snet-workload-prd"; "data" = @{ "parent" = "/subscriptions/1x11x11x-11x1-111x-1x11-11111111x11x/resourceGroups/rg-network-horizoncloud/providers/Microsoft.Network/virtualNetworks/vnet-westeurope-horizoncloud"; "name" = "snet-workload-prd"; "availableIpAddresses" = 251; "cidr" = "10.21.3.0/24" } }; } "name" = "UAG"; "orgId" = "xxx11x11-1111-xx1x-1111-1111x11xx111"; "providerInstanceId" = "111x1xx1x1x1xx11xx111111"; "numberOfGateways" = 2; "sslCertificate" = @{ "data" = @{ "certificate" = "-----BEGIN CERTIFICATE-----"; "certificatePassword" = "" }; "type" = "PEM" } "type" = "EXTERNAL" } Invoke-RestMethod -Uri "https://cloud.vmwarehorizon.com/admin/v2/uag-deployments" -Method Post -Headers $Header -Body ($Body | ConvertTo-Json -Depth 5) |
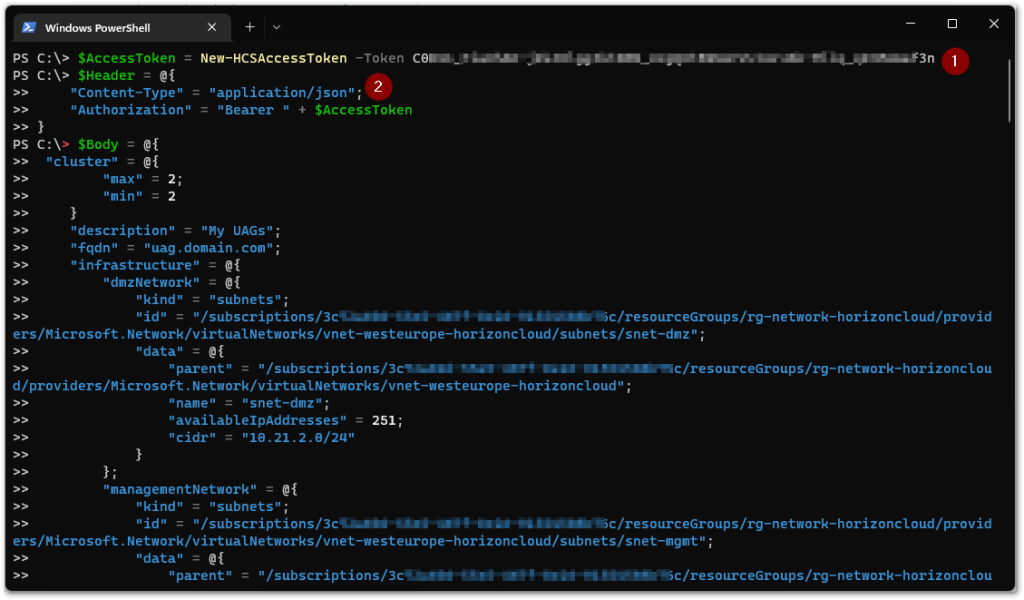
(1) We create the access token from the API token using the New-HCSAccessToken function we described in chapter 2. We put this value in the $AccessToken variable, which we will use in the following step.
(2) We then construct the $Header array, where we specify the expected Content-Type to be received by the URI, which is application/json. And we specify the type of authorization using the Bearer type with the access token from the variable $AccessToken.
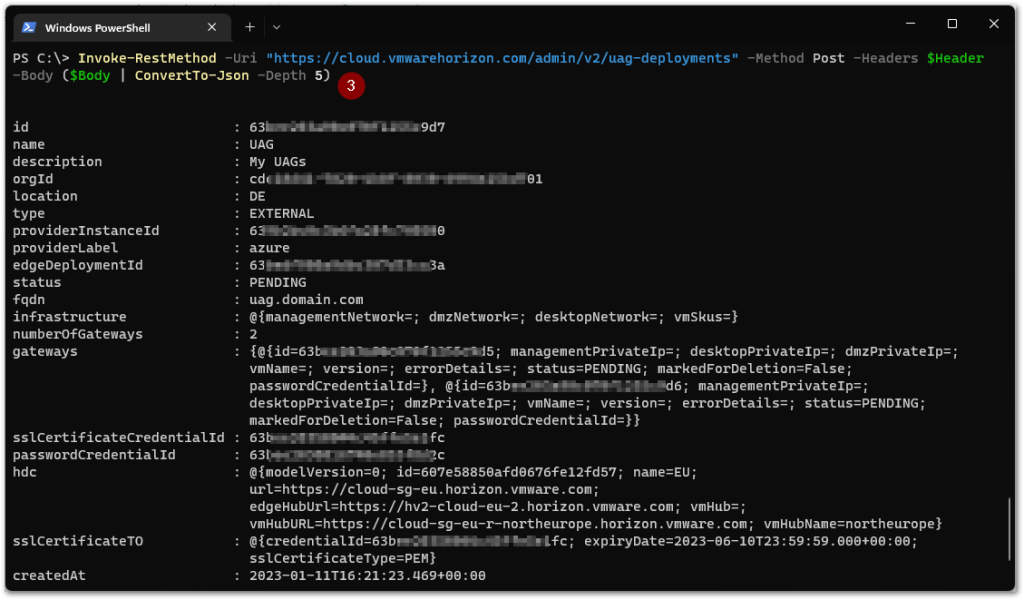
(3) We execute the command to add the Unified Access Gateway configuration (3). Once executed, the output with what has been configured will be displayed.
Get
To retrieve the Unified Access Gateway configuration(s), we will use the following information:
| HTTP Method | GET | |
| URI | https://cloud.vmwarehorizon.com/admin/v2/uag-deployments | |
| Content-Type | application/json | Header |
| Authorization | Bearer <Access token> | Header |
With this information we will now construct the lines of code in PowerShell to retrieve the Unified Access Gateway configuration(s).
|
1 2 3 4 5 6 |
$Header = @{ "Content-Type" = "application/json"; "Authorization" = "Bearer " + $AccessToken } Invoke-RestMethod -Uri https://cloud.vmwarehorizon.com/admin/v2/uag-deployments -Method Get -Headers $Header |
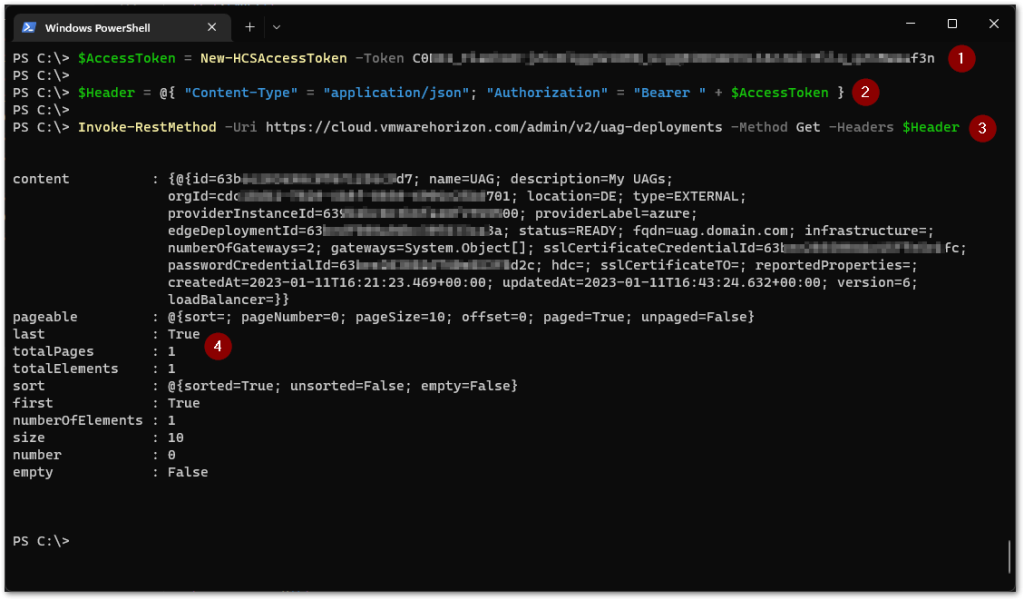
(1) We create the access token from the API token again using the New-HCSAccessToken function, and put this value in the $AccessToken variable, which we will use in the following step.
(2) We construct the $Header array, where we specify the expected Content-Type to be received by the URI, which is application/json. And we specify the type of authorization using the Bearer type with the access token from the variable $AccessToken.
(3) We execute the command to retrieve the Unified Access Gateway configuration(s).
(4) Once executed, the output with what has been configured will be displayed.
Delete
To delete a Unified Access Gateway configuration, we will use the following information:
| HTTP Method | DELETE | |
| URI | https://cloud.vmwarehorizon.com/admin/v2/uag-deployments | |
| Content-Type | application/json | Header |
| Authorization | Bearer <Access token> | Header |
| id | Id number for the Unified Access Gateway deployment | URI |
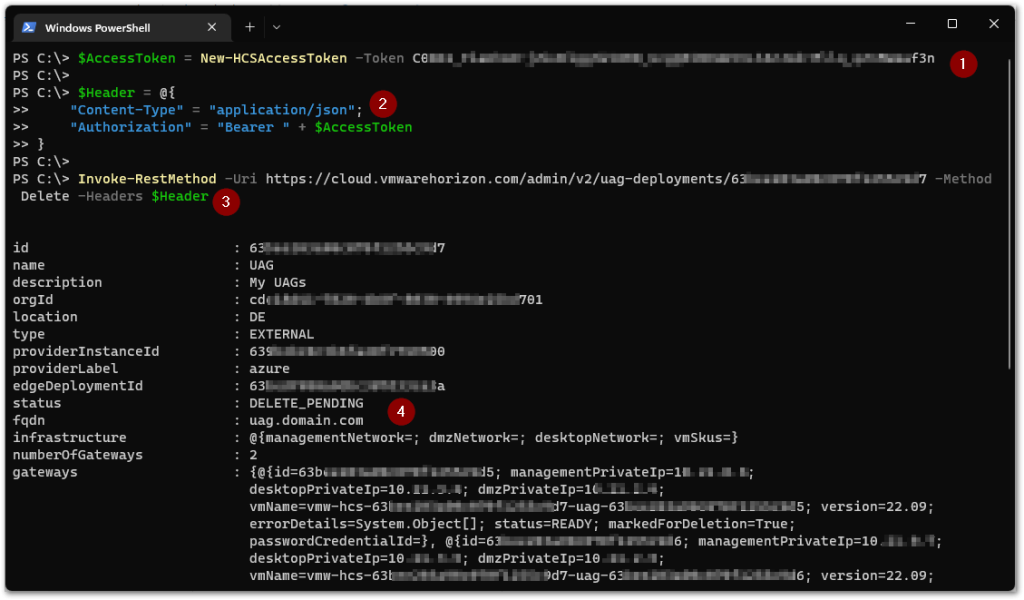
(1) We create the access token from the API token again using the New-HCSAccessToken function, and put this value in the $AccessToken variable, which we will use in the following step.
(2) We construct the $Header array, where we specify the expected Content-Type to be received by the URI, which is application/json. And we specify the type of authorization using the Bearer type with the access token from the variable $AccessToken.
(3) We execute the command to delete the Unified Access Gateway configuration.
(4) Once executed, the output with what has been deleted will be displayed.
PowerShell Functions Examples
| The scripts below serve as examples. You may change the scripts to your own needs or standards, like error handling, securing password strings and things like that. |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 |
Function New-HCSUAGDeployment { [CmdletBinding()] param ( [Parameter(Mandatory=$True)] [string]$AccessToken, [Parameter(Mandatory=$False)] [string]$URI, [Parameter(Mandatory=$True)] [string]$OrganizationId, [Parameter(Mandatory=$True)] [string]$Name, [Parameter(Mandatory=$False)] [string]$Description, [Parameter(Mandatory=$True)] [string]$FQDN, [Parameter(Mandatory=$True)] [int]$NumberOfGateways, [Parameter(Mandatory=$True)] [string]$SSLCertificate, #must be PEM format (no PFX), including key and root/intermediates [Parameter(Mandatory=$True)] [string]$ManagementSubnetId, [Parameter(Mandatory=$True)] [string]$ManagementSubnetParent, [Parameter(Mandatory=$True)] [string]$ManagementSubnetName, [Parameter(Mandatory=$True)] [string]$ManagementSubnetAvailableIPAddresses, [Parameter(Mandatory=$True)] [string]$ManagementSubnetCIDR, [Parameter(Mandatory=$True)] [string]$DMZSubnetId, [Parameter(Mandatory=$True)] [string]$DMZSubnetParent, [Parameter(Mandatory=$True)] [string]$DMZSubnetName, [Parameter(Mandatory=$True)] [string]$DMZSubnetAvailableIPAddresses, [Parameter(Mandatory=$True)] [string]$DMZSubnetCIDR, [Parameter(Mandatory=$True)] [string]$WorkloadSubnetId, [Parameter(Mandatory=$True)] [string]$WorkloadSubnetParent, [Parameter(Mandatory=$True)] [string]$WorkloadSubnetName, [Parameter(Mandatory=$True)] [string]$WorkloadSubnetAvailableIPAddresses, [Parameter(Mandatory=$True)] [string]$WorkloadSubnetCIDR, [Parameter(Mandatory=$True)] [string]$ProviderInstanceId ) If (!($URI)) { $URI = "https://cloud.vmwarehorizon.com/admin/v2/uag-deployments" } $Header = @{ "Content-Type" = "application/json"; "Authorization" = "Bearer " + $AccessToken } $Body = @{ "cluster" = @{ "max" = $NumberOfGateways; "min" = $NumberOfGateways } "description" = "$Description"; "fqdn" = "$FQDN"; "infrastructure" = @{ "dmzNetwork" = @{ "kind" = "subnets"; "id" = $DMZSubnetId; "data" = @{ "parent" = $DMZSubnetParent; "name" = $DMZSubnetName; "availableIpAddresses" = $DMZSubnetAvailableIPAddresses; "cidr" = $DMZSubnetCIDR } }; "managementNetwork" = @{ "kind" = "subnets"; "id" = $ManagementSubnetId; "data" = @{ "parent" = $ManagementSubnetParent; "name" = $ManagementSubnetName; "availableIpAddresses" = $ManagementSubnetAvailableIPAddresses; "cidr" = $ManagementSubnetCIDR } }; "desktopNetwork" = @{ "kind" = "subnets"; "id" = $WorkloadSubnetId; "data" = @{ "parent" = $WorkloadSubnetParent; "name" = $WorkloadSubnetName; "availableIpAddresses" = $WorkloadSubnetAvailableIPAddresses; "cidr" = $WorkloadSubnetCIDR } }; } "name" = "$Name"; "orgId" = "$OrganizationId"; "providerInstanceId" = "$ProviderInstanceId"; "numberOfGateways" = $NumberOfGateways; "sslCertificate" = @{ "data" = @{ "certificate" = "$SSLCertificate"; "certificatePassword" = "" }; "type" = "PEM" } "type" = "EXTERNAL" } Invoke-RestMethod -Uri "$URI" -Method Post -Headers $Header -Body ($Body | ConvertTo-Json -Depth 5) -UseBasicParsing } |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 |
Function Get-HCSUAGDeployment { [CmdletBinding()] param ( [Parameter(Mandatory=$True)] [string]$AccessToken, [Parameter(Mandatory=$False)] [string]$URI, [Parameter(Mandatory=$False)] [string]$Name ) If (!($URI)) { $URI = "https://cloud.vmwarehorizon.com/admin/v2/uag-deployments" } $Header = @{ "Content-Type" = "application/json"; "Authorization" = "Bearer " + $AccessToken } If (!($Name)) { Write-Output (Invoke-RestMethod -Uri "$URI" -Method Get -Headers $Header -UseBasicParsing).content } Else { ForEach ($_ in (Invoke-RestMethod -Uri "$URI" -Method Get -Headers $Header -UseBasicParsing).content) { If ($_.name -eq "$Name") { Write-Output $_ $NameFound = $True } } If ($NameFound -ne $True) { Write-Warning "Name not found." } } } |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 |
Function Remove-HCSUAGDeployment { [CmdletBinding()] param ( [Parameter(Mandatory=$True)] [string]$AccessToken, [Parameter(Mandatory=$False)] [string]$URI, [Parameter(Mandatory=$True)] [string]$Id, [Parameter(Mandatory=$False)] [bool]$Force ) If (!($URI)) { If ($Force -eq $True) { $URI = "https://cloud.vmwarehorizon.com/admin/v2/uag-deployments/" + "$Id" + "?force=true" } Else { $URI = "https://cloud.vmwarehorizon.com/admin/v2/uag-deployments/" + "$Id" } } $Header = @{ "Content-Type" = "application/json"; "Authorization" = "Bearer " + $AccessToken } Invoke-RestMethod -Uri "$URI" -Method Delete -Headers $Header -UseBasicParsing } |
I hope this chapter was informative and that you enjoyed reading.
This concludes the automation series for now. In the future I will create standalone posts on different Horizon Cloud next-gen automation topics.